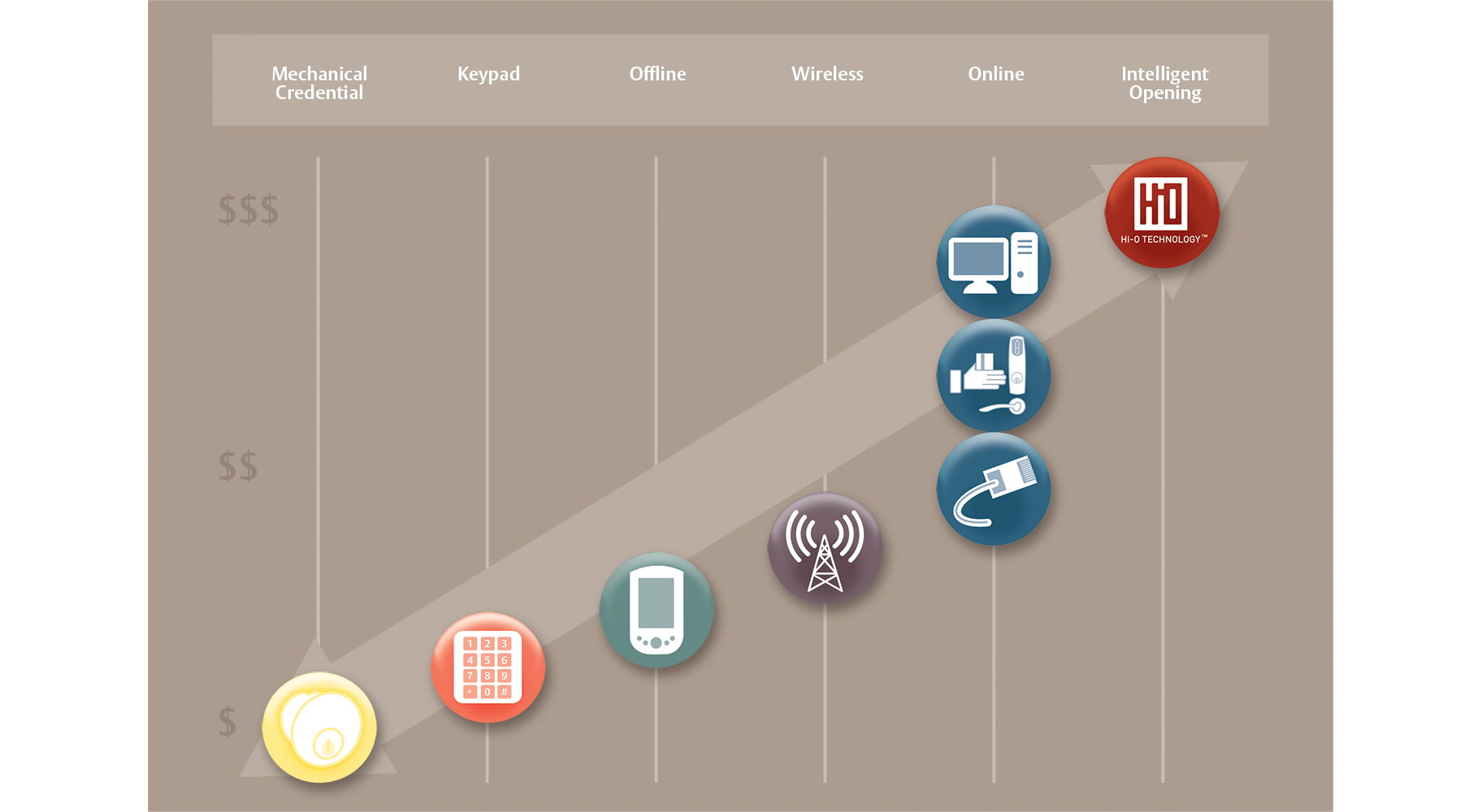
Access Control of the Past
Access control is a general term used in security to reference the act of granting, limiting, or removing access to an asset, usually a door. For hundreds of years, a traditional lock and key were the only means of access control. Keys worked 24 hours a day, 365 days a year, and you didn't know who used them and when. If you wanted to guarantee a user no longer had access to a door, you had to rekey or replace the lock and issue new keys to everyone that should still have access.
Access Control Today
Today, we have a lot more tools at our disposal. Locks have become more sophisticated, and so have electronic access control products. There are a host of options to consider when selecting the best product for each door. Locks are still standard on every door, but as the need for security increases, higher levels of security can be added.
Mechanical Credentials
“Mechanical credential” is just a fancy term which essentially means a key. Keys come in three generic categories: standard security, restricted key control, and high security restricted key control. Learn more about keys and other lock products on our Commercial Locks page. While a keyed lock is still standard on every door you want to limit access to, keys have limitations.
Mechanical Credential Limitations
- There are no time constraints on access. A key works 24 hours a day and can't be limited to certain times of the day or days of the week. You can see where this might be an issue if you want to keep someone out during times they shouldn't have access.
- Even with a restricted key control system, if you don't get a key back from someone who should no longer have access, your only remedy to guarantee that person can't get in anymore is to rekey or replace the lock and then issue new keys to everyone who should still have access to that door. This can be a costly endeavor and gets more expensive as you add more doors to your system.
- There can be significant delays to removing someone’s access. While we do perform locksmith services such as rekeys, you still need to wait for us to arrive and perform the work before the old access is terminated. Then, depending on your keying setup, you may need to hand out new keys to everyone you still want to have access. There are more sophisticated options listed below that can terminate access immediately without affecting anyone else.
Keypad Locks
 Keypad locks are the first level of more sophisticated access control. They come in a few different configurations with varying options. In general a keypad lock gains you the ability to issue users unique codes. When you wish to terminate access to a user you can delete that user’s code and they no longer have access. An example of a keypad lock product is the Yale inTouch Keypad Lock.
Keypad locks are the first level of more sophisticated access control. They come in a few different configurations with varying options. In general a keypad lock gains you the ability to issue users unique codes. When you wish to terminate access to a user you can delete that user’s code and they no longer have access. An example of a keypad lock product is the Yale inTouch Keypad Lock.
Keypad Lock Advantages
- Affordable upgrade into more sophisticated access control than just keys.
- Fast and simple installation.
- Management of granting access isn’t through keys.
- Some offer the use of biometric features such as hand geometry readers, finger print readers, or iris scan readers.
Keypad Lock Limitations
- Programming typically happens by visiting each door.
- Management of users can be cumbersome. You generally need to keep a written log matching each user to a code and a specific slot in the memory you programmed it in to remove access for someone.
- In order to get audit trails, you usually need to go to the lock with some sort of download device such as a pda and retrieve the information.
- The lock’s memory is often limited to a certain number of recent events which get written over as you reach your data limit. If you wait too long to recover your audit trail, a specific event you’re researching may be gone.
- Giving a user access to multiple doors requires you to manually program that user’s code into each door separately. Each lock tends to be an independent entity and they are not aware of other locks in the system.
Offline Locks
Offline locks are a middle ground between keypad locks and online locks. They offer some (but not all) of the higher level features of Online Locks but offer some up front cost savings compared to online locks. An example of an offline lock product is the Sargent Profile Series v.G1.5.
Offline Lock Advantages
- You can use an electronic credential such as a proximity or iclass card which is more secure than a keypad code.
- Software based programming is available for keeping track of data such as users, access rights, and audit trails.
- While more expensive than a keypad lock, these locks are not wired back to a head end controller like an online lock so up front installation costs are less.
- Programming a card to gain access to more than one door does not require a visit to each of those doors.
Offline Lock Limitations
- Locks are not physically connected to a door controller so there can be lag time between when events occur and when that audit trail data is accessible.
- Lag time can also occur between when changes in programming are entered on the server and when they actually take effect at the door.
- The audit trail is either stored in the credential or in the offline lock instead of a in a central database on a server.
- In order to extract audit trail information when stored in an offline credential, it often needs to be programmed to periodically expire and go out of service. The user of that credential must then reactivate the credential at a designated reader that is “online”. While the credential is being reactivated, the audit trail is extracted.
- In order to extract audit trail information when stored in an offline lock, the lock gathers the data locally and only sends it to the server at designated times programmed ahead of time. If you need real-time data without being able to wait, this can be a problem.
- The ability to “lock down” a facility during an extreme event can either be delayed or may not be available at all.
Online Locks
In an online lock, there is a connection between the door being controlled and a system sever that is tracking events and access rights in real time.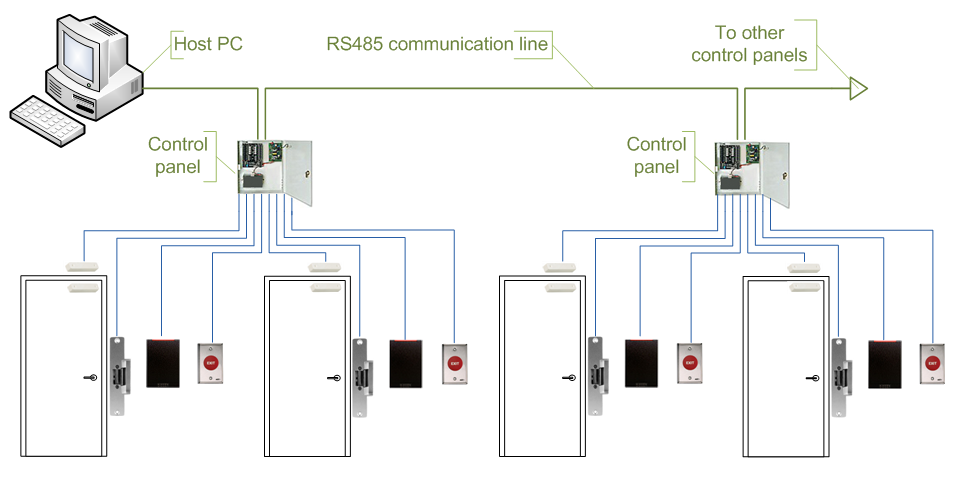
Online Lock Advantages
- You can use an electronic credential such as a proximity or iclass card which is more secure than a keypad code.
- You can also use biometric readers such as hand geometry readers, finger print readers, or iris scan readers.
- Programming a card to gain access to more than one door does not require a visit to each of those doors.
- Software based programming is available for keeping track of data such as users, access rights, time periods, holidays, and audit trails.
- Data changes and audit trails happen in real time so there are no delays.
- Multiple sites can all be programmed remotely without needing to visit the sites.
- Lock downs in an emergency are convenient and instant.
- Offers the most amount of convenience and features in ongoing system administration once installed.
Online Lock Limitations
- Wires need to be run from the lock to a door controller and the door controller needs to be connected to the system server, which is sometimes local and sometimes “in the cloud”.
- Online locks tend to be the most expensive option compared to the alternatives previously described.
Wireless Locks
Wireless locks generally have all the features of an Online Lock system but are used when getting wires to individual doors can be tricky. We can design a system to use a combination of Wireless and Online Locks.
Wireless Lock Advantages
- Usually all the same advantages of Online Locks.
- Wires don’t need to be run from the controller to the lock.
- Can be used on the same system with Online Locks.
- Can sometimes be a cost saver if you need the features of an online lock but getting a wire to the door would be difficult or impossible.
- You can track assets not suitable for online lock products such as cabinet doors, desk drawers, and server cabinets.
Wireless Lock Limitations
- The parts for wireless locks are more expensive than the parts for a wired online lock, (However, their use may still save you money in situations where installing a wired online lock would involve a high labor cost.)
- Typically components that are separate devices in an online lock suck as the lock, the door position contact, and the request to exit switch are built into one unit in a wireless lock. If any one of the three fail in a wireless lock, you need to pay to replace all three rather than just that one part.
REQUEST A QUOTE
If you're ready to get started adding access control to your business, or if you need us to answer questions you may have, call us at 413-SECURITY (732-8748). If you prefer we reach out to you, fill out this form and we'll be in touch as soon as we can.